Well… all this RFID stuff wasn’t all just because I was trying to be a maker person…. nope, there was still the hacker/pen tester in me that was driving all this RFID shenanigans. I built something, it was actually something I built before I made the RFID holocron raspberry Pi RDM6300 thing….
First I want to give credit where credit is due, I basically used the notes from this wonderful info sec individual named Alex Dib and his post on the RFID Thief v2.0 – Here another great post Here and it is all based on the Wiegotcha code found Here.
Parts:
– Raspberry Pi 3 – I also made a variation using a Raspberry Pi Zero W but more on that latter – I also got one working with a Raspberry Pi 2 but needed a USB wifi dongle to go into AP mode
– HID MaxiProx 5375 – got mine used off Ebay, they didn’t know if it worked or not so I got a better deal but it still wasn’t “Cheap”
– Logic Level Converter
– Battery Pack – car jumper (12v out) with USB ports – 12v for the MaxiProx and USB for the Raspberry pi
– Electronics jumper wires – basically just wire since I did end up soldering it all together anyway
– Tape and glue, you don’t want things moving around too much….
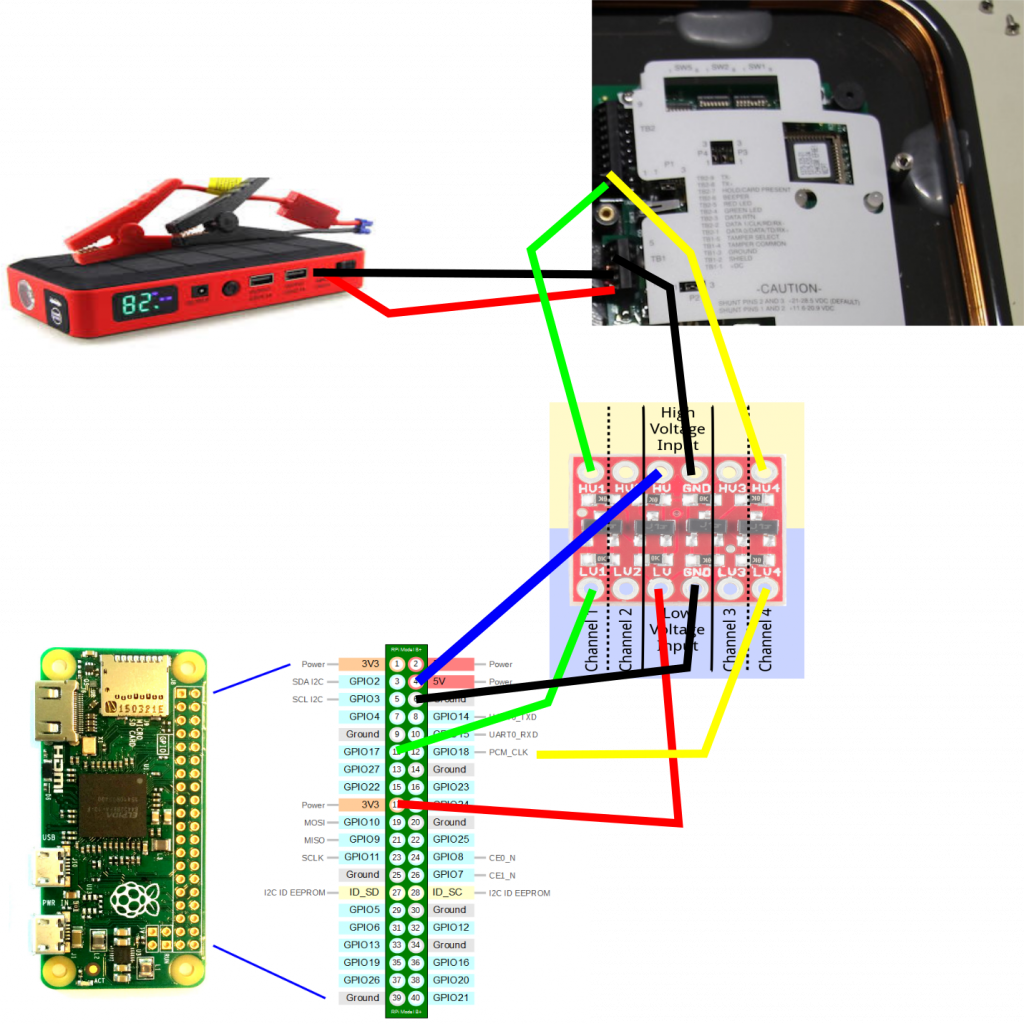
Raspberry Pi Pins:
– Pin 4 (5v) – Level Shifter HV
– Pin 6 (Ground) – LV Ground
– Pin 11 (GPIO 17) – LV Channel 1
– Pin 12 (GPIO 18) – LV Channel 4
– Pin 17 (3.3v) – LV
Level Shifter Pins:
– HV Channel 1 – HID TB2-1 (Data 0)
– HV Channel 4 – HID TB2-2 (Data 1)
– HV Ground – HID TB1-2 (Shield)
Battery Pins:
– USB – to raspberry Pi
– 12v+ – to HID TB1-1
– 12v- – to HID TB1-3
clone the Wiegotcha code
git clone https://github.com/lixmk/Wiegotcha
cd Wiegotcha
./install.shYou will answer some questions and reboot, then run:
./laststep.shNow after you reboot again – make sure you verify my instructions (per the links above) I did this a while ago and am just now writing this all down….
Now power it on and connect:
Default Passwords:
- root:Wiegotcha
- pi:Wiegotcha
IP Addressing:
- eth0 = DHCP
- wlan0 = 192.168.150.1
Access Point:
- ESSID: Wiegotcha
- Pass: Wiegotcha
Navigate to http://192.168.150.1 via browser.